Explain Different Kinds of Online Threats Class 10 It
In order to protect yourself you need to know about the different ways in which your computer can be compromised and your privacy infringed. A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers.

7 Types Of Cyber Security Threats
After a worm affects a host it is able to spread very quickly over the network.
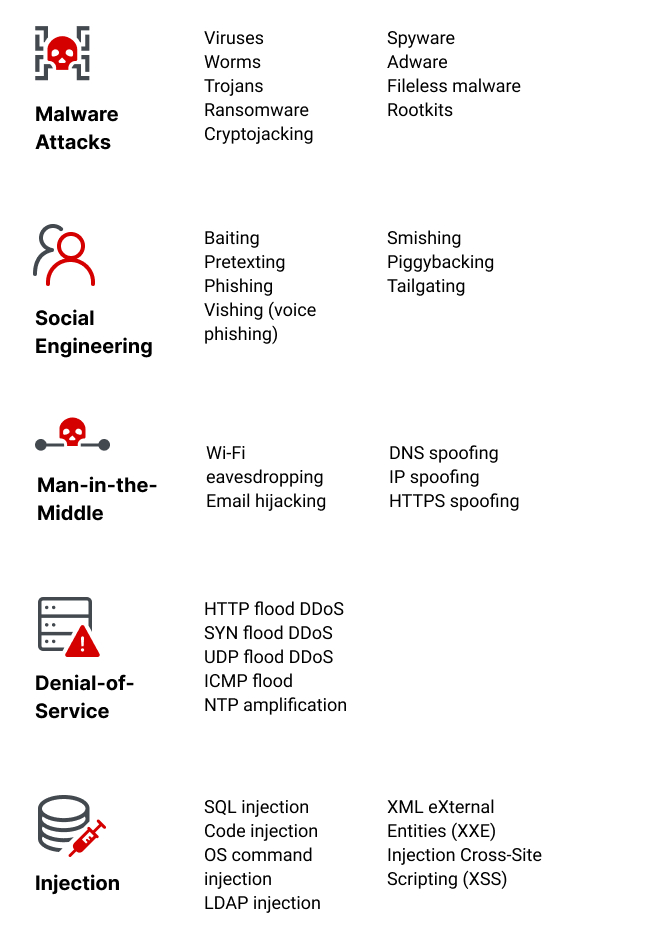
. Threats can be classified into four different categories. Bullying is most often recognized as a form of physically and verbally aggressive behavior that school children endure from their peers. Biological diversity largely describes the change of life from genes to ecosystems comprising their existences genetic variations their environment populations and the ecosystem in which they are existing and other evolutionary developments that keep the system functioning changing and adapting.
A cyber attack is a type of attack that targets computer systems using various methods at hands. The main threat can be of online frauds. Trojan horses spyware adware ransomware phishing viruses worms rootkits and browser hijackers are all types of malware.
Anything that one downloads from the internet can have hidden malware inside. 5 Most Common Types of Threats You Need to Know About. Cybercriminals are carefully discovering new ways to tap the most sensitive networks in the world.
This can include cyberstalking distributing pornography and trafficking. Threat can be anything that can take advantage of a vulnerability to breach security and negatively alter erase harm object or objects of interest. How to prioritize threats.
An indirect threat tends to be vague unclear and ambiguous. These types of bullying overlap and a bully may use more than one. Malicious software comes in many forms such as viruses Trojan horses spyware and worms.
Malware is defined by its malicious intent acting against the requirements of the computer user and does. This is the least common cybercrime but. Spyware collects information and sends it to the hacker.
For UPSC 2021 preparation follow BYJUS. In addition three SHAP methods are used to explain the output of the resulting machine learning models for the five-class data sets. The efficacy of these models performance was evaluated by measuring the precision recall F1-score accuracy and confusion matrix.
The OWASP threat model. Short for malware spam or malicious spam malspam is a spam message that delivers malware to your device. Up to 20 cash back The malware could contain anything from a banking Trojan to a bot short for robot.
A direct threat identifies a specific target and is delivered in a straightforward clear and explicit manner. Download PDF notes for free. What are cybersecurity threats.
The 12 types of Cyber Crime. DDoS MitM social engineering and more. A bot is software designed to perform whatever tasks the hacker wants it to.
The plan the intended victim the motivation and other aspects of the threat are masked or equivocal. Short for malicious software malware comes in several forms and can cause serious damage to a computer or corporate network. The era of online payment gateways has arrived and due to this a lot of payment frauds have also entered the scene.
The banking Trojan watches your online activity to steal more details from you often your bank account information including your password. Mobile Device Security Threats. Malware a portmanteau of malicious software is any software used to disrupt computer operation gather sensitive information or gain access to private computer systems.
Know the various types of cyber attacks. Information Security threats can be many like Software attacks theft of intellectual property identity theft theft of equipment or information sabotage and information extortion. Its purpose is to steal private information from a computer system for a third party.
Unsuspecting readers who click on a link or open an email attachment end up with some type of malware including ransomware Trojans bots info-stealers cryptominers spyware and keyloggers. This category of cybercrime involves one individual distributing malicious or illegal information online. Protecting business data is a growing challenge but awareness is the first step.
Common sources of cybersecurity threats. Physical threats to mobile devices most commonly refer to the loss or theft of a device. Cybersecurity trends and challenges.
In this post you will learn. To detect cybersecurity threats. Data security is another inline threat under which your personal data is.
Mobile Network Security Threats. Here are the top 10 threats to information security. This article explores cybercrime in depth so that you know exactly what threats you need to protect yourself against to stay safe online.
Network-based threats are especially common and risky because cybercriminals can steal unencrypted data while people use public WiFi networks. Malware is usually picked up from the internet or through ones email. Types of Bullying.
However there are actually six different kinds of bullying. Trojan horse worms virus spyware are some of the different types of online threats. Different kinds of online threats.
Modern technology and societys constant connection to the Internet allows more creativity in business than ever before including the black market. Physical verbal relational cyber sexual and prejudicial. Using threat intelligence for threat prevention.
A Trojan horse or Trojan is a type of malicious code or software that looks legitimate but can take control of your computer. Direct indirect veiled conditional. A virus needs a host program to run but worms can run by themselves.
Understanding exactly what cybercrime is the different types and how to protect yourself from it will help put your mind at rest.

8 Most Common Cybersecurity Threats Types Of Cyber Attacks Cybersecurity For Beginners Edureka Youtube

No comments for "Explain Different Kinds of Online Threats Class 10 It"
Post a Comment